The growing popularity of cloud computing in the dynamic landscape of modern digital infrastructure has caused a profound shift in how companies navigate the realms of data management and storage. As organizations progressively alter their operational frameworks to cloud environments, the need for robust and all-encompassing security measures, especially the shared responsibility model provided by AWS, becomes increasingly crucial. The significant shift to cloud-based solutions offered by AWS has ushered in a new epoch of unrivaled convenience and operational competency, paralleled by an onslaught of intricate security challenges that demand elaborate scrutiny. This requires exacting deliberation and enactment strategies for enhancing the general security posture of digital ecosystems in this perpetually evolving tech landscape and firmly adhering to the shared responsibility between AWS and the AWS customers in relation to cloud security and compliance.
In the first installment of this blog series, we will look at the most common security concerns in cloud computing. Our primary focus will be on understanding the complexities of the most common security challenges and determining the best AWS services to effectively address and mitigate these issues.

What is Cloud Security and Why is It Important?
Cloud security refers to the use of cutting-edge technologies and safety practices in order to safeguard data, apps, and the cloud computing infrastructure. It is essential to provide cloud security since it guarantees your data and apps are accessible to authorized users. Potential security vulnerabilities can be quickly addressed with effective cloud security measures in place, providing peace of mind.
When choosing a cloud security model, there are three main options to consider: public, private, and hybrid cloud. Here are the key differences between them:
- Public Cloud: This cloud computing model is distributed and shared between enterprises via the Internet. Public clouds are popular among small and medium-sized organizations, startups, and individual users because they are highly scalable, cost-effective, and provide a wide range of services.
- Private Cloud: A single organization owns, manages, and maintains this cloud computing model. Private clouds provide higher security, compliance, and adaptable control, making them ideal for organizations with sensitive data or strict regulatory requirements. They can be hosted on-site or at a third-party data center.
- Hybrid Cloud: This cloud computing model combines private and public cloud features. It enables organizations to use the public cloud for non-essential data or workloads while keeping crucial applications and sensitive data in the private cloud. Hybrid clouds provide the flexibility of public clouds while also providing the security and management of private clouds.
Consider factors such as security requirements, cost, scalability, and regulatory requirements when deciding on a cloud model. A hybrid cloud model may be the best option for organizations that want to take advantage of public cloud cost savings while maintaining a higher level of security or compliance for specific services.
Cloud Security Statistics
As the cloud security landscape unfolds, let’s explore key statistics shaping the narrative, offering insights into the challenges and dynamics of securing digital realms.
- Million Insights: Before delving into the numbers, it’s worth noting that the global cloud security market, which was valued at 7.1 billion in 2019, is expected to grow by 2027, at a CAGR of 14.64%.
- Data Breach: Despite the impressive growth, a troubling trend emerges: 39% of companies experienced at least one cloud data breach in the previous 12 months, according to Thales, highlighting the ongoing challenges in securing cloud environments.
- Access Challenges: As organizations increasingly migrate to the cloud, access control becomes increasingly important. Surprisingly, the majority of Chief Information Security Officers (CISOs) faced a major challenge: determining excessive access to sensitive data in cloud environments.
- Cloud Adoption: The adoption of cloud services is a dominant force, with a staggering 94% of enterprise organizations now hosting at least some of their IT environment in the cloud, reflecting a transformative shift in the technology landscape.
- Hybrid Cloud Trend: In navigating the cloud landscape, a notable trend emerges—76% of organizations leverage the flexibility of multiple public clouds, while 42% strategically design cloud-based applications tailored specifically for this dynamic environment.
Challenges and Concerns
Before going into the critical challenges and concerns surrounding cloud security, let’s examine some compelling statistics that highlight the evolving complexities in safeguarding data and applications in the cloud.
- Top Challenges: As organizations embrace the cloud, they face several challenges. Controlling costs (40%), ensuring data privacy/security (38%), securing cloud resources (31%), adhering to governance/compliance (30%), and dealing with a shortage of cloud security skills/expertise (30%) are all significant obstacles.
- Security Threats: When it comes to the potential pitfalls of public clouds, the top security threats stand out—misconfiguration (68%), unauthorized access (58%), insecure interfaces (52%), and account hijacking (50%) are all significant risks that call for alert mitigation.
- Staffing Issues: Even as technology advances, staffing remains a critical bottleneck. An unexpected 37% of security professionals identify a lack of qualified staff as a significant impediment to rapid cloud adoption, shedding light on the ongoing struggle to keep up with evolving security demands.
Best Practices and Solutions
To ensure the security of your applications, consider the following best practices:
- Design for Security: Incorporate security into your application from the beginning. Utilize secure coding practices and frameworks while maintaining security requirements at the forefront during the design phase.
- Choose a Secure Cloud Provider: Select a reputable cloud provider that offers robust security features like access controls, encryption, and network security. Examine the security certifications and compliance reports provided by the provider.
- Monitoring Data: Data monitoring is essential for cloud security since it enables detection and response to potential breaches of security and other issues inside your cloud environment. Select monitoring technologies that are suited for your needs and environment, such as Amazon CloudWatch, Azure Monitor, and Google Cloud Monitoring.
- Gaining Visibility: Gaining visibility into cloud security is critical for ensuring the security and dependability of your cloud resources. To gain a single perspective of your cloud environment, use centralized logging to collect and integrate log data from different sources. This makes it easier to identify potential security concerns and vulnerabilities.
- Managing Access: Access management is an important part of cloud security since it ensures that only authorized users and services have access to your cloud resources. To authenticate the identity of users and services accessing your cloud resources, use strong authentication mechanisms such as multi-factor authentication (MFA) or biometric authentication. Control access to your cloud resources with Role-Based Access Control (RBAC) based on user roles and responsibilities. Following the principle of least privilege, provide users and services the minimum level of access required to execute their tasks.
AWS Cloud Security
Recognizing the importance of data security in the cloud, it is essential to prioritize strong security measures for cloud computing when using AWS (Amazon Web Services). It is critical to recognize that compliance is a shared responsibility, emphasizing the collaborative effort required by AWS and the customer to maintain both security and regulatory standards. This shared model ensures that operational responsibilities are distributed, with AWS managing components ranging from the host operating system to physical security, while the customer is responsible for the guest operating system, application software, and AWS security group firewall configuration.
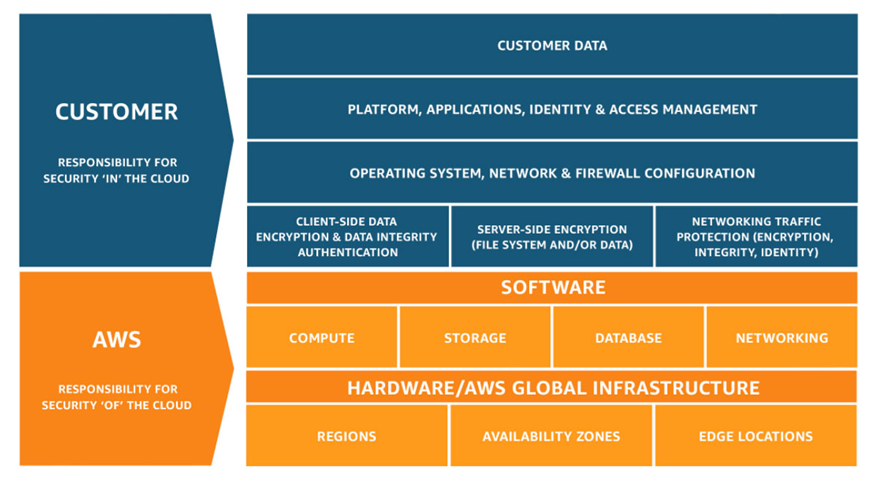
With its wide set of cloud-based services and resources, AWS requires a thorough security strategy. In the following sections of this blog article, we will break down the complexities of AWS security, concentrating on four main categories in the following order:
- AWS IAM Policies and Roles
- AWS Networking
- AWS Logging and Monitoring
- Database Storage Security
AWS IAM Policies and Roles
AWS roles and policies have a critical role in establishing cloud security. By setting granular permissions and using IAM roles, companies can implement the concept of least privilege and enhance their protection against unwanted access and privilege abuse. We will emphasize the importance of AWS roles and policies in enhancing security and outline best practices for establishing a secure and resilient security framework within AWS environments.
In the following section, we will look at the most common security concerns and how you address them while utilizing the following services: AWS Identity and Access Management (IAM), AWS Key Management Service (KMS), and AWS Certificate Manager (ACM).
| Security Concern | Recommended AWS Configurations/Best Practice |
| Least Privilege Principle | IAM Policies: Apply the principle of least privilege by creating IAM policies that allow only the permissions that are required for a user, group, or role to perform their specific tasks. Granting broad, unnecessary permissions should be avoided. |
| Credential Exposure | IAM Roles: Use IAM roles to securely grant permissions for Amazon EC2 instances, Lambda functions, and other AWS services. When possible, avoid using access and secret keys. Rotate access and secret keys on a regular basis. |
| Unauthorized Access | AWS Identity and Access Management (IAM): Implement strict IAM policies to manage access to AWS resources. For an additional layer of user authentication, take into account Multi-Factor Authentication (MFA). |
| Cross-Account Access | AWS Organizations and IAM Roles: Use AWS Organizations to group multiple AWS accounts. Implement cross-account IAM roles to securely grant access across accounts while maintaining resource segregation. |
| IAM Policy Monitoring and Auditing | AWS CloudTrail along with Amazon CloudWatch: Enable AWS CloudTrail to log IAM events. Use CloudWatch to monitor IAM events, set up alerts for unexpected activity, and evaluate and audit IAM policies regularly to guarantee compliance and security. |
| Lack of IAM Password Policies | IAM Password Policies: Define and implement IAM password policies to ensure secure and strong passwords. Set constraints for password length, complexity, and expiration to improve the overall security of IAM users. |
| Privilege Escalation | IAM Roles and AWS Security Token Service (STS): To decrease the risk of privilege escalation, utilize STS and IAM roles to implement temporary security credentials. Passwords should be rotated regularly, and temporary credentials should be limited in duration. |
| Inactive User Accounts | AWS Identity and Access Management (IAM): Perform regular reviews and audits of IAM user accounts. Disable or deactivate inactive user accounts to avoid any security issues connected with unused or unnecessary credentials. |
| Unsecured Access Keys | AWS Key Management Service (KMS): Use KMS to manage and rotate IAM access keys’ encryption keys. Rotate access and secret keys on an ongoing basis to reduce the risk of unauthorized access and subsequent exposure. |
| Lack of IAM Role Assumption Restrictions | IAM Role Assumption Policies: Limit IAM role assumption by specifying trusted entities (AWS accounts, IAM users, roles) that can assume the role. This helps in the prevention of unwanted access and ensures proper management. |
| IAM Policy Versioning and Change Control | IAM Policy Versioning and Change Management: Implement IAM policy versioning and change management techniques. Review and audit policy modifications regularly to ensure that they are in line with security best practices and compliance standards. |
AWS Networking
When it comes to the topic of networking, as companies use Amazon Virtual Private Cloud (VPC), AWS Transit Gateway, and AWS VPN to provide seamless integration and data transfer across their cloud infrastructure, ensuring strong security through AWS networking services is important. Organizations can secure sensitive information, restrict unauthorized access, and maintain the integrity of their network design by emphasizing security in AWS networking.
Next, we will look at the main security concerns and effective techniques for addressing them when using the previously mentioned AWS networking services. Companies can enhance their AWS networking settings, guaranteeing a resilient and secure foundation for their cloud operations, by completely understanding and proactively addressing these issues.
| Security Concern | Recommended AWS Configurations/Best Practice |
| Data Interception | Virtual Private Cloud (VPC): VPC allows you to set up a logically isolated section of the AWS Cloud from which you can launch AWS resources in a virtual network. Encrypt data in transit with SSL/TLS. |
| DDoS Attacks | AWS Shield: Managed Distributed Denial of Service (DDoS) protection service designed to safeguard AWS-hosted applications from both infrastructure and application layer DDoS attacks. |
| Network Traffic Monitoring | Amazon CloudWatch: Use CloudWatch to monitor network traffic for insights into resource utilization, identify unusual patterns, and configure alerts for potential security incidents. |
| Unsecured APIs | Amazon API Gateway: Amazon API Gateway secures APIs and allows you to develop, publish, and manage APIs. To control access, use authentication and authorization mechanisms such as API keys or OAuth. |
| Man-in-the-Middle Attacks | AWS Certificate Manager (ACM): ACM is a service that allows you to provision, manage, and deploy SSL/TLS certificates for your applications. Encrypt communication with Secure Sockets Layer (SSL) or Transport Layer Security (TLS). |
| Insider Threats | AWS CloudTrail: Enable AWS CloudTrail to log, continually monitor, and retain account activity associated with AWS infrastructure activities. Set up notifications for any suspicious activities or changes. |
| Lack of Network Segmentation | Security Groups and Network ACLs: Within a VPC, use security groups and network ACLs to govern inbound and outbound traffic, implement network segmentation, and restrict communication between different parts of your network. |
| Lack of Redundancy and High Availability | Elastic Load Balancing (ELB) and Amazon Route 53: Use Route 53 for domain registration and DNS services. To provide high availability and fault tolerance, use ELB to distribute incoming traffic across multiple instances. |
AWS Logging and Monitoring
Moving on, we’ve reached the subject of logging and monitoring, including AWS CloudWatch, AWS CloudTrail, and Amazon Elasticsearch Service. The significance of AWS’s comprehensive logging and monitoring cannot be overstated. As companies rely on these services to observe and analyze their cloud environments, safeguarding the security of this data becomes a top priority. In the following part of the article, we will explore common security concerns and effective techniques for addressing them when utilizing these key AWS services.
| Security Concern | Recommended AWS Configurations/Best Practice |
| Unauthorized Access | AWS CloudTrail: Enable AWS CloudTrail to log all API calls made on your account. This provides specific details about who executed the call, the services used, and when the call was made, helping you in tracking and investigating unauthorized access. |
| Anomalous Activity Detection | AWS Config with Amazon CloudWatch: Use CloudWatch to monitor and set alarms for unusual activity patterns, such as sudden rises in traffic or resource utilization. AWS Config assists you in assessing, auditing, and evaluating your resources’ setups. |
| Data Breach Detection | Amazon GuardDuty together with AWS CloudTrail: CloudTrail logs provide a trail of events that may be examined to detect and investigate suspected data breaches. GuardDuty is a managed threat detection service that monitors for malicious behavior in real-time. |
| Insufficient Resource Monitoring | Amazon CloudWatch: Set up Amazon CloudWatch to monitor the performance of your AWS resources to discover resource bottlenecks and potential security risks, monitor metrics such as CPU utilization, disk I/O, and network traffic. |
| Lack of Visibility into API Activities | AWS CloudTrail: CloudTrail logs API activities, providing visibility into actions performed through your AWS account. This contains information such as who made the API call, the source IP address, and when the call took place, which improves your ability to monitor API usage. |
| Inadequate Incident Response | AWS CloudWatch Alarms and AWS Config Rules: Define CloudWatch Alarms to notify you of potential security incidents. AWS Config Rules enable you to set up automated responses to non-compliant configurations, helping you respond quickly to security events. |
| Log Tampering | AWS CloudTrail and Amazon S3 Versioning: Store CloudTrail logs in an S3 bucket with versioning enabled. This assures that logs are immutable, and any attempts to tamper with or remove logs may be identified and investigated. |
| Inadequate Log Retention | Amazon S3 Lifecycle Policies with AWS CloudWatch Logs: Configure CloudWatch Logs to keep logs for the necessary amount of time. Using S3 lifecycle policies, you can automatically move logs to long-term storage or delete them based on your retention settings. |
| Lack of Centralized Logging | Amazon CloudWatch Logs and AWS CloudWatch Logs Insights: Collect logs from several AWS services and store them in CloudWatch Logs for centralized storage. CloudWatch Logs Insights can be used to query and analyze logs from several sources in a unified manner. |
| Inefficient Resource Utilization Alerts | Amazon CloudWatch Alarms: Configure CloudWatch Alarms to get notifications when resource utilization metrics exceed thresholds that are predetermined. This allows you to work with resource issues and any security threats before they become a cause for concern. |
| Lack of Real-time Monitoring | Amazon CloudWatch Events and AWS Config Rules: CloudWatch Events allow you to respond to changes in your AWS environment in real-time. Use AWS Config Rules to continuously monitor and assess the configurations of your resources in near real-time. |
Database Storage Security
Transitioning to the next subject of database and storage security, which is another critical component of any organization’s digital infrastructure. With a growing reliance on services such as Amazon Relational Database Service (RDS), Amazon DynamoDB, Amazon Aurora, S3, EBS, and EFS for sensitive data storage and management, ensuring the security of these databases is critical. In the following section, we will look at the most common security concerns and effective techniques for dealing with them when using these critical AWS services. Companies may protect their valuable data, limit the risk of unauthorized access, and increase the overall integrity of their storage infrastructure by prioritizing security in database storage.
| Security Concern | Recommended AWS Configurations/Best Practice |
| Unauthorized Access | Amazon RDS Security Groups: Use security groups to control inbound and outbound traffic to your Amazon RDS instances. Restrict access to only necessary IP addresses and configure secure connections using protocols like SSL/TLS. |
| Data Encryption at Rest | Amazon RDS Encryption: Using AWS Key Management Service (KMS), enable encryption at rest for your RDS instances. This ensures that data on disk is encrypted, providing an additional layer of security against unauthorized access. |
| Data Encryption in Transit | Amazon RDS SSL/TLS: Encrypt data in transit between your application and Amazon RDS instances using SSL/TLS. Enabling encryption for database connections assists in the security of sensitive data as it passes between the client and server. |
| Database Auditing and Logging | Amazon RDS Enhanced Monitoring and Amazon CloudWatch Logs: To capture performance metrics, enable Enhanced Monitoring for your RDS instances. Configure CloudWatch Logs to store database logs, enabling auditing and analysis of database activity. |
| Lack of Database Activity Monitoring | Amazon RDS Performance Insights: Monitor and analyze database activities with Performance Insights. It provides a complete view of the database load and assists in identifying the most frequently executed SQL queries, making it easier to detect and troubleshoot any security issues. |
| Database Backups and Disaster Recovery | Amazon RDS Automated Backups and Snapshots: Enable automated backups for RDS instances to create regular backups of your database. Manually take snapshots for point-in-time recovery. Using Multi-AZ deployments, you create an effective disaster recovery plan. |
| Insufficient Access Control | AWS IAM Database Authentication: Use database Authentication to centrally manage database access for RDS instances. This approach allows the use of IAM roles and rules to restrict access to the database, thereby enhancing access control and security. |
| SQL Injection | Amazon RDS Parameter Groups and Database Firewall Rules: To configure security settings for your RDS instances, use parameter groups. Implement database firewall rules to regulate incoming traffic, restrict access, and prevent SQL injection attacks. |
| Unpatched Database Software | Amazon RDS Automated Software Patching: Enable automated software patching for RDS instances to keep your database software up to date with the most recent security patches. This helps to protect against known vulnerabilities while also improving overall security. |
| Data Exfiltration Prevention | Amazon RDS IAM Roles and VPC Endpoints: Control access to other AWS services from your RDS instances through the use of IAM roles. Use VPC endpoints to enable a secure connection between your RDS database and other AWS resources, lowering the chance of data exfiltration/leaks. |
| Lack of Database Activity Auditing | AWS CloudTrail and Amazon RDS Logs: Enable CloudTrail to capture API activity related to your RDS instances. Additionally, configure RDS to log database events to provide a complete audit trail of database activities, facilitating investigative examination if necessary. |
| Inadequate Database Patch Management | Amazon RDS Automated Software Patching: To ensure that critical security patches are applied as soon as possible, enable automated software patching for RDS instances. Monitor for database vulnerabilities on a regular basis and apply patches to address potential security risks. |
Conclusion
After going into the important categories, you’ve obtained insights into efficiently safeguarding your AWS environment and identifying the most appropriate services for certain situations. As we end this chapter, stay tuned for the next part of our series, in which we will delve deeper into practical guides for doing extensive security scans and addressing specific issues. Our journey through AWS security best practices continues, providing you with actionable strategies to secure your cloud infrastructure against evolving threats.

