Introduction
We all know what Single sign-on (SSO) stands for, or it is the authentication method that allows us to use only one set of credentials to sign in multiple resources and applications. This feature increases resource usage as it makes it easier and faster for users to log in. The main benefit of SSO is that users can authenticate and personalize easily without the need to transmit any personal data over the web. Users will only need to authenticate themselves once per session unless they switch browsers, clear cookies, or use a new device. SSO can support automatic personalization where end-users have immediate access to their personal folder and settings when logging in.
Experience SSO 2.0 for yourself
Built with the enterprise in mind, SSO 2.0 takes single sign-on to the next level, making it easier to manage, more fluid, and more secure than ever. ( https://www.atlassian.com/blog/crowd/single-sign-on)
As enterprises continuously grow and transform each day, so do their applications and services. A user’s identity has become significantly important as an organizational asset these days, and as a result, a new type of system known as an identity provider (IDP’s), where users’ identities are stored and authenticated is created. Essentially IDPs is a trusted system that allows users to use a single sign-on (SSO) to access their systems, applications, and other services.
Authentication Login Standards
SAML – A web-based model that allows third-party applications or services to validate the user’s identity and retrieve details about a certain user.
SCIM – Identity management standard that establishes a common way to manage user accounts and privileges across applications.
Open ID Connect – Simple Identity layer that is on top of the OAuth 2.0 protocol.
Recently we’ve been put up with a task to integrate an Atlassian Jira & Confluence instance with SSO authentication platform OneLogin. A SAML authentication protocol was chosen because it is supported by both Atlassian and OneLogin identity providers.
Configuration Steps
Prerequisites:
- Atlassian instance requires at least one verified domain for the organization
- The chosen Atlassian product and the identity provider should use HTTPS protocol for communication
- Temporary user with an email account that is outside the organization domain in case SAML has been misconfigured
- Configuration user requires site and organization admin access
OneLogin & Atlassian Configuration
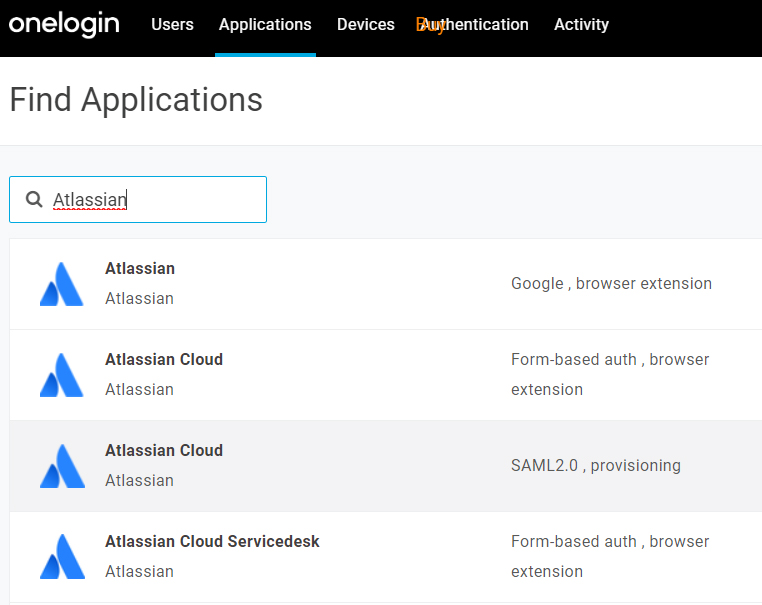
1. Find the Atlassian Cloud app using SAML 2.0 protocol
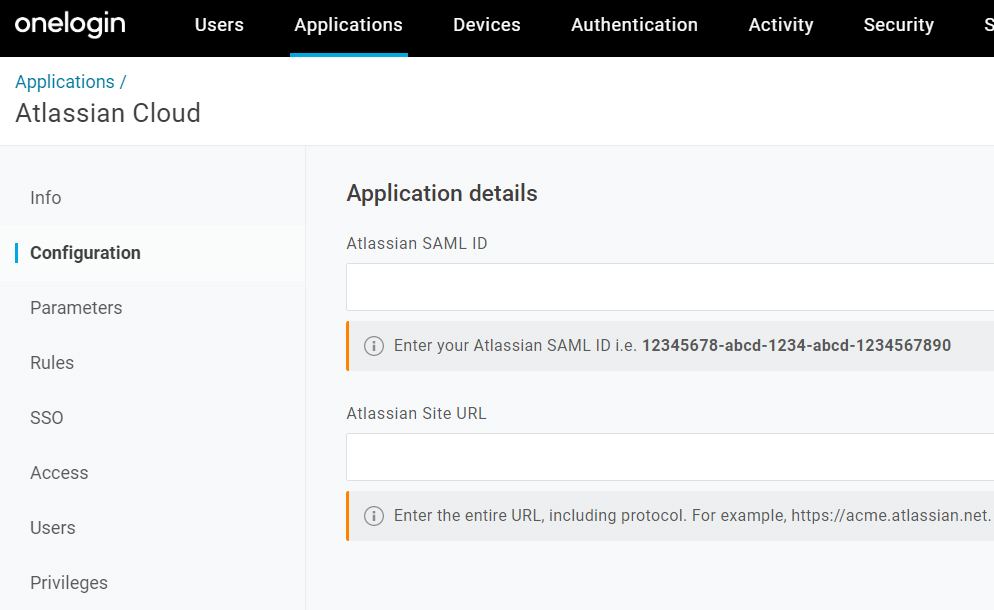
2. In the Configuration tab set Atlassian SAML ID and the Site URL, both values can be found in the Atlassian Instance
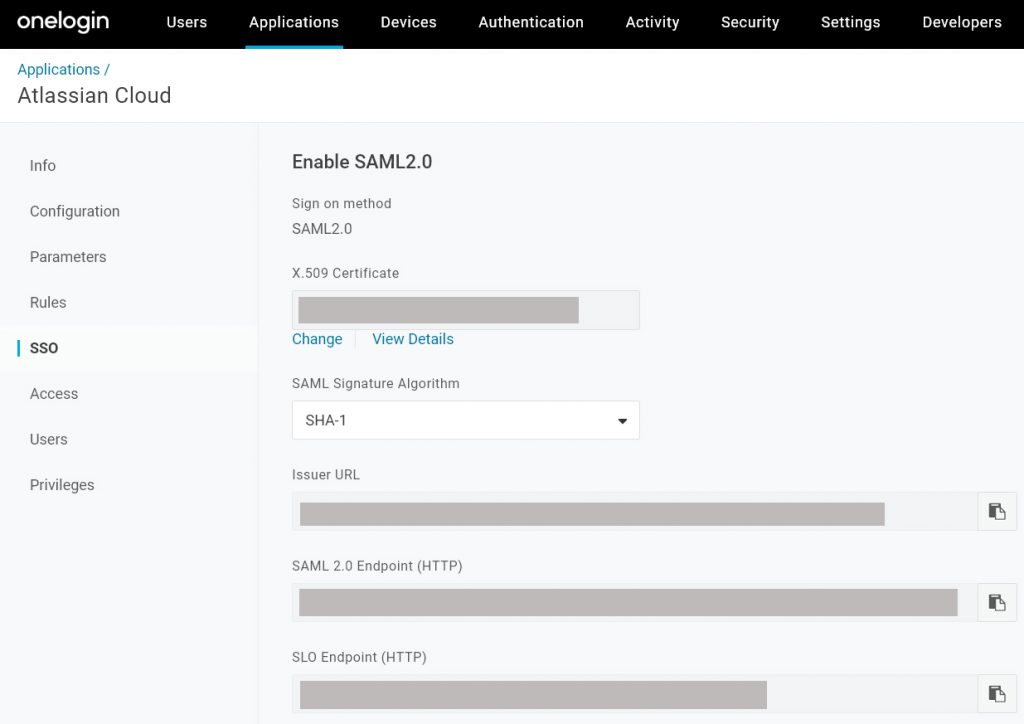
3. From the SSO tab extract and import required values into SAML, Security, Atlassian Administration panel (x509 Certificate, Identity provider Entity ID and SSO URL)
4. In the OneLogin user Dashboard Atlassian applications should be shown with access to configured products
Conclusion
We can conclude that single sign-on can improve user experience, and boost productivity and efficiency by eliminating the process of logging into applications separately and having a password for each one of them.
From an organizational perspective implementing a well-organized SSO strategy can help reduce help desk requests and IT support costs and improve security and compliance. Overall having SSO is an essential solution for a sizable enterprise.

