Introduction to API Security Testing with OWASP ZAP
Zed Attack Proxy (or ZAP for short) is a free, open-source penetration testing tool being maintained under the umbrella of the Open Web Application Security Project (or OWASP). ZAP is designed to find security vulnerabilities in your web application. ZAP also supports security testing of APIs, GraphQL and SOAP.
Installation of OWASP ZAP
In this blog you can find the instructions on how to use OWASP ZAP with Docker and Jenkins. First, we need to install the following applications:
- Download OWASP ZAP from https://www.zaproxy.org/download/ and run the installation.
- Dowload Docker Destkop from https://www.docker.com/products/docker-desktop
- Download Jenkins from https://www.jenkins.io/download/
Note that ZAP and Jenkins require Java 8 or higher in order to run.
OWASP ZAP Docker Image
With OWASP ZAP you can perform manual security scans using the ZAP UI. In our previous blog post, we explained the process of security scan of web applications with the ZAP UI. The steps for security scanning of APIs are similar to web application scans. Check our blog post Introduction to Security Testing with OWAS ZAP to find out more.
In this blog post, we will explain the steps of an automated approach to security testing using Docker image with the OWASP ZAP tool preinstalled and integration with Jenkins.
OWASP ZAP docker Image installation instructions:
docker pull owasp/zap2docker-stable – get the stable release.
docker pull owasp/zap2docker-weekly – get the latest weekly release.
docker pull owasp/zap2docker-live – get the live release (built whenever zaproxy project is changed).
docker pull owasp/zap2docker-bare – get the bare release (a very small Docker image that contains only the necessary dependencies that are required to run ZAP, ideal for CI environments).
Docker image contains python scripts for active scan, passive scan etc.
There are two types of scan that can be performed with ZAP:
- Passive Scan – Passive scaning doesn’t change the requests and responses and is safe to use. Passive scaning is good for finding issues like missing security headers or missing anti CSRF tokens but it is no good for finding vulnerabilities like XSS (cross-site scripting) that requires malicious requests to be sent – for that purpose should be used active scanning.
The passive scan can be done with zap-baseline.py script, it can perform scans against the APIs defined by OpenAPI, SOAP, or GraphQL. For the passive scan use the following command:
docker run -t owasp/<docker-image-release> zap-baseline.py -t <api-endpoint>
The command above will perform passive scan that reports any issues found to the command line. In order to generate report with the scan results use the following command:
docker run -v $(pwd):/zap/wrk/:rw -t owasp/<docker-image-release> zap-baseline.py -t <api-endpoint> -r <name-of-report>.html
Docker command is explained below:
-t – target API definition, OpenAPI or SOAP, local file or URL.
-v $(pwd):/zap/wrk/:rw – is a docker option that maps the current working directory to a folder called /zap/wrk.
-r – is a Docker option to write in a file the full ZAP HTML report
-x – is a Docker option to write in a file the full ZAP XML report
-J – is a Docker option to write in a file the full ZAP JSON document
Note: All Docker options for writing the report in the file can be used.
- Active Scan – The difference between passive and active scanning is that active scan performs known attacks on the target application to find potential vulnerabilities. Active scanning is a real attack and it should not be used if you have no permission to test.
The active scan can be done with zap-api-scan.py script. The active scan can be performed with the following command:
docker run -t owasp//<docker-image-release> zap-api-scan.py -t <api-endpoint> -f openapi -r <name-of-report>.html
OWASP ZAP Jenkins Setup
Setup on Jenkins is easy and the whole setup is done in the “Execute Windows batch command” build step.
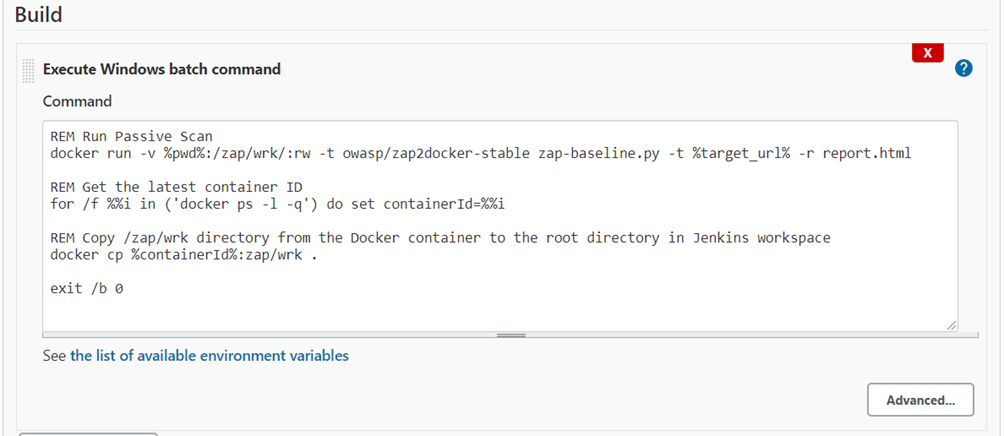
After the build is finished, an email with HTML report will be sent.
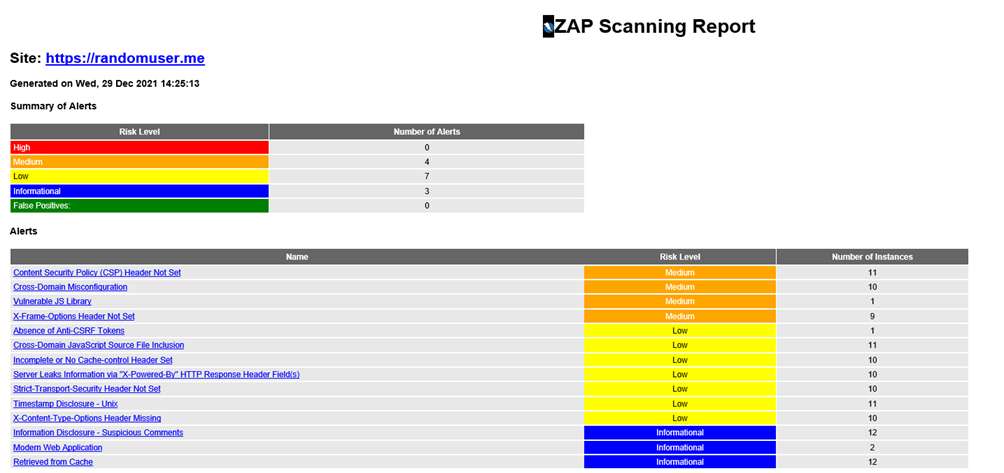
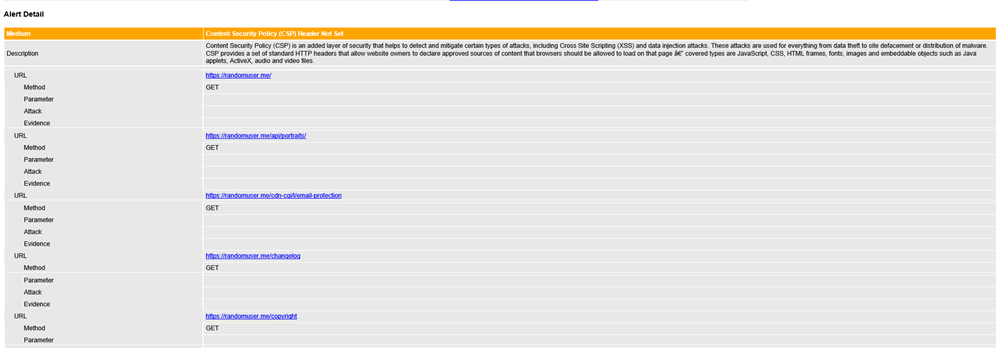
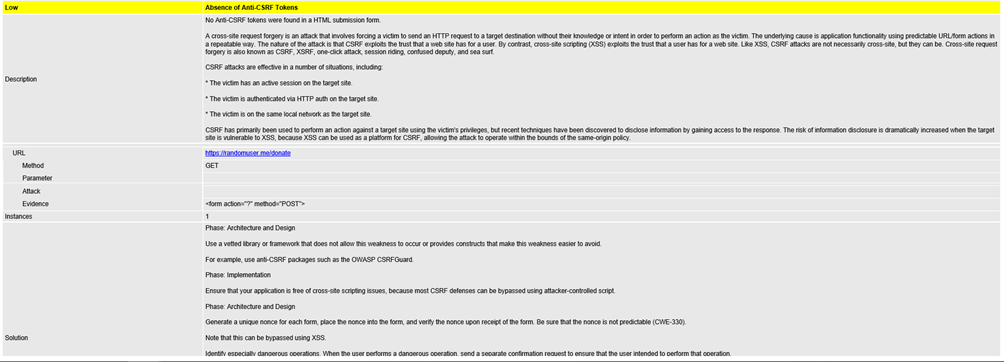
OWASP ZAP Reporting
ZAP HTML report is very descriptive and provides solutions for potential security risks. Security alerts are divided by the risk level. ZAP HTML report contains a description, URL, and solution for each alert.
Conclusion
OWASP ZAP provides an easy way to automate the security scanning of APIs using OpenAPI definition, SOAP, or GraphQL. The scan can be done from a simple command line, the scan is also very similar for SOAP and GraphQL. It also provides a detailed HTML, JSON, or XML report that contains the description of the alert, risk level, and possible solution.

